INSURGE INTELLIGENCE, a new crowd-funded investigative journalism project, breaks the exclusive story of how the United States intelligence community funded, nurtured and incubated Google as part of a drive to dominate the world through control of information. Seed-funded by the NSA and CIA, Google was merely the first among a plethora of private sector start-ups co-opted by US intelligence to retain ‘information superiority.’
Tag Archives: Google
Type The Wrong Thing Into A Search Engine And The Secret Police Will Come Knocking On Your Door
(Michael Snyder) - The control freaks are out of control. Once upon a time America was “the land of the free”, but now it has become “the land of the bureaucrats”, and these bureaucrats are absolutely obsessed with watching, tracking, monitoring and controlling virtually everything that you do. Last month, I wrote about how the Obama administration forced a small-time magician out in Missouri to submit a 32 page disaster plan for the little rabbit that he uses in his magic shows for kids. A lot of people thought that story was quite humorous, but the examples in this article are not so funny. In recent days we have learned that the government is monitoring just about everything that we do on the Internet, and we have also learned that a couple of innocent Google searches can result in armed government agents pounding on your front door. If you do not believe this, read on… Continue reading
Google Pressure Cookers and Backpacks, Get a Visit from the Feds

Michele Catalano was looking for information online about pressure cookers. Her husband, in the same time frame, was Googling backpacks. Wednesday morning, six men from a joint terrorism task force showed up at their house to see if they were terrorists. Which prompts the question: How’d the government know what they were Googling? Continue reading
Google, Microsoft Speak Out on Gov. Requests; New Firefox Plug-in Informs Users of NSA Spying

On Friday, Facebook’s general council member Ted Ullyot publically announced that his company had been inquired by various local and federal government agencies to provide personal information of up to 10,000 users within the last six months of 2012. In all, those 10,000 demands implicated up to 19,000 personal Facebook user accounts. Continue reading
Yahoo to Users: Let Us Read Your Emails or — Goodbye!
Startpage.com
June 1, 2013
As of June 1, all Yahoo email users are required to upgrade to the company’s newest platform, which allows Yahoo to scan and analyze every email they write or receive. According to Yahoo’s help page, all users who make the transition agree to let the company perform “content scanning and analyzing of your communications content” to target ads, offer products, and perform “abuse protection.”
This means any message that Yahoo’s algorithms find disturbing could flag a user as a bully, a threat, or worse. At the same time, Yahoo can now openly troll through email for personal information that it can share or hold onto indefinitely. See:http://help.yahoo.com/kb/index?page=content&y=PROD_MAIL_ML&locale=en_US&id=SLN3254
Archived at: Yahoo mail upgrade.
Gay and haven’t come out yet? Yahoo knows. Having an affair? Your spouse may not know — but Yahoo does. Any interests, ailments or projects you’d rather not share? You’re sharing them with Yahoo, perhaps forever.
The new tracking policy affects more than just Yahoo account holders. Everyone who corresponds with a Yahoo email account holder will also have their own message content scanned, analyzed, and stored by Yahoo, even if they themselves have not agreed to Yahoo’s new terms of service.
“Emailing through Yahoo means surrendering your privacy, whether it’s your own account or your friend’s,” says Harvard-trained privacy expert Katherine Albrecht, who is helping to develop StartMail, an upcoming email service that will not scan its users’ correspondence. “It’s time we start paying attention to these policies, because they’re growing more shockingly abusive every day,” she added.
Where prior versions of Yahoo had tracking policies buried in the fine print, the company’s tracking agenda is now openly stated in paragraph 2: “When you upgrade you will be accepting our …Privacy Policy.” That is, its anti-privacy policy.
Concerned Yahoo users are invited to check out StartMail, a completely private email program slated for release this Fall. Anyone who would like to be a beta tester can visit StartMail (www.StartMail.com) and sign up for the upcoming release.
Rest assured: That information will not be shared with anyone at all.
Especially not Yahoo.
For further details, please contact:
Katherine Albrecht, Ed.D.
U.S. Media Relations
StartMail Private Email // StartPage & Ixquick Private Search
www.StartMail.com // www.StartPage.com // www.Ixquick.com
+1 877-434-3100 ext. 5 [toll free] +1 973-273-2125 [International]
E.U. Contact Person:
Alex van Eesteren
Sales & Business Development
StartMail Private Email // StartPage & Ixquick Private Search
www.StartMail.com // www.StartPage.com // www.Ixquick.com
+31-30-6971778
The U.S. Government Is Monitoring All Phone Calls, All Emails And All Internet Activity

Big Brother is watching everything that you do on the Internet and listening to everything that you say on your phone. Every single day in America, the U.S. government intercepts and stores nearly 2 billion emails, phone calls and other forms of electronic communication. Former NSA employees have come forward and have described exactly what is taking place, and this surveillance activity has been reported on by prominent news organizations such as the Washington Post, Fox News and CNN, but nobody really seems to get too upset about it. Either most Americans are not aware of what is really going on or they have just accepted it as part of modern life. But where will this end? Do we really want to live in a dystopian “Big Brother society” where the government literally reads every single thing that we write and listens to every single thing that we say? Is that what the future of America is going to look like? If so, what do you think our founding fathers would have said about that?
Many Americans may not realize this, but nothing that you do on your cell phone or on the Internet will ever be private again. According to the Washington Post, the NSA intercepts and stores an astounding amount of information every single day…
Every day, collection systems at the National Security Agency intercept and store 1.7 billion e-mails, phone calls and other types of communications. The NSA sorts a fraction of those into 70 separate databases.
But even the Washington Post may not have been aware of the full scope of the surveillance. In fact, National Security Agency whistleblower William Binney claims that the NSA has collected “20 trillion transactions” involving U.S. citizens…
In fact, I would suggest that they’ve assembled on the order of 20 trillion transactions about U.S. citizens with other U.S. citizens.
And NSA whistleblowers have also told us that the agency “has the capability to do individualized searches, similar to Google, for particular electronic communications in real time through such criteria as target addresses, locations, countries and phone numbers, as well as watch-listed names, keywords, and phrases in email.”
So the NSA must have tremendous data storage needs. That must be why they are building such a mammoth data storage center out in Utah. According to Fox News, it will have the capability of storing 5 zettabytes of data…
The NSA says the Utah Data Center is a facility for the intelligence community that will have a major focus on cyber security. The agency will neither confirm nor deny specifics. Some published reports suggest it could hold 5 zettabytes of data. (Just one zettabyte is the equivalent of about 62 billion stacked iPhones 5?s– that stretches past the moon.
Are you outraged by all of this?
You should be.
The U.S. government is spying on the American people and yet they continue to publicly deny that they are actually doing it.
Last week, this government spying program was once again confirmed by another insider. What former FBI counterterrorism agent Tim Clemente told Erin Burnett of CNN is absolutely astounding…
BURNETT: Tim, is there any way, obviously, there is a voice mail they can try to get the phone companies to give that up at this point. It’s not a voice mail. It’s just a conversation. There’s no way they actually can find out what happened, right, unless she tells them?
CLEMENTE: “No, there is a way. We certainly have ways in national security investigations to find out exactly what was said in that conversation. It’s not necessarily something that the FBI is going to want to present in court, but it may help lead the investigation and/or lead to questioning of her. We certainly can find that out.
BURNETT: “So they can actually get that? People are saying, look, that is incredible.
CLEMENTE: “No, welcome to America. All of that stuff is being captured as we speak whether we know it or like it or not.”
Yes, “all of that stuff” is most definitely being “captured” and it is time for the Obama administration to be honest with the American people about what is actually going on.
Meanwhile, the recent bombing in Boston has many of our politicians calling for even tighter surveillance.
For example, New York City Mayor Michael Bloomberg recently said that our interpretation of the U.S. Constitution will “have to change” to deal with the new threats that we are facing. More “smart cameras” are going up in New York, and Bloomberg says that we are “never going to know where all of our cameras are”. The following is from a recent RT article…
New York City police officials intend to expand the already extensive use of surveillance cameras throughout town. The plan, unveiled Thursday, comes as part of a drive for increased security around the US following the Boston Marathon attack.
New York City Police Department Commissioner Ray Kelly announced the plan during a press conference with Mayor Michael Bloomberg, in which the two announced that the suspected Boston Marathon bombers were planning to attack New York next. The pair said they hope to discourage criminals by using so-called “smart cameras” that will aggregate data from 911 alerts, arrest records, mapped crime patterns, surveillance cameras and radiation detectors, among other tools, according to The Verge.
“You’re never going to know where all of our cameras are,” Bloomberg told reporters gathered outside City Hall. “And that’s one of the ways you deter people; they just don’t know whether the person sitting next to you is somebody sitting there or a detective watching.”
Will you feel safer if the government is watching you 100% of the time?
Do you want them to see what you are doing 100% of the time?
You might want to think about that, because that is where all of this is headed.
In fact, the truth is that spy cameras are not just going up all over New York City. Most Americans may not realize this, but a network of spy cameras is now going up all over the nation. The following is an excerpt from one of my previous articles…
“You are being watched. The government has a secret system – a machine – that spies on you every hour of every day.” That is how each episode of “Person of Interest” on CBS begins. Most Americans that have watched the show just assume that such a surveillance network is completely fictional and that the government would never watch us like that. Sadly, most Americans are wrong. Shocking new details have emerged this week which prove that a creepy nationwide network of spy cameras is being rolled out across the United States. Reportedly, these new spy cameras are “more accurate than modern facial recognition technology”, and every few seconds they send back data from cities and major landmarks all over the United States to a centralized processing center where it is analyzed. The authorities believe that the world has become such a dangerous place that the only way to keep us all safe is to watch what everyone does all the time. But the truth is that instead of “saving America”, all of these repressive surveillance technologies are slowly killing our liberties and our freedoms. America is being transformed into an Orwellian prison camp right in front of our eyes, and very few people are even objecting to it.
For many more examples of how the emerging Big Brother surveillance grid is tightening all around us, please see my previous article entitled “19 Signs That America Is Being Systematically Transformed Into A Giant Surveillance Grid“.
Meanwhile, Barack Obama is telling us to reject those that are warning us about government tyranny. The following is what he told the graduating class of The Ohio State University on May 5th, 2013…
Unfortunately, you’ve grown up hearing voices that incessantly warn of government as nothing more than some separate, sinister entity that’s at the root of all our problems. Some of these same voices also do their best to gum up the works. They’ll warn that tyranny always lurking just around the corner. You should reject these voices.
So what do you think?
Should we just ignore all of the violations of our privacy that are happening?
Should we just ignore what the U.S. Constitution says about privacy and let the government monitor us however it wants to?
Read more at http://investmentwatchblog.com/the-u-s-government-is-monitoring-all-phone-calls-all-emails-and-all-internet-activity/#vLT5zSVSEKcqHuIQ.99
Department of Justice secretly gave Internet service providers immunity when conducting surveillance
 According to documents obtained by the Electronic Privacy Information Center (EPIC), the Department of Justice secretly authorized the interception of electronic communications on certain parts of AT&T and other Internet service providers’ networks.
According to documents obtained by the Electronic Privacy Information Center (EPIC), the Department of Justice secretly authorized the interception of electronic communications on certain parts of AT&T and other Internet service providers’ networks.
Previously, EPIC obtained documents on the National Security Agency’s Perfect Citizen program which involves monitoring private computer networks. This latest revelation deals with an entirely different program first called Defense Industrial Base Cyber Pilot, or DIB Cyber Pilot, though it is now operating as Enhanced Cybersecurity Services.
While this type of activity might be illegal under federal wiretapping legislation, the Obama administration gave the companies immunity when monitoring networks under a cybersecurity pilot program.
“The Justice Department is helping private companies evade federal wiretap laws,” said Marc Rotenberg, executive director of EPIC. “Alarm bells should be going off.”
The alarm bells should get louder when one realizes that while this collaboration between the Department of Defense (DoD), the Department of Homeland Security (DHS) and the private sector began focusing only on defense contractors, the program was massively expanded.
Thanks to an executive order dated February 12, 2013 entitled, “Improving Critical Infrastructure Cybersecurity,” the program was widened significantly.
The order expanded it to cover other “critical infrastructure industries” which includes “systems and assets, whether physical or virtual, so vital to the United States that the incapacity or destruction of such systems and assets would have a debilitating impact on security, national economic security, national public health or safety, or any combination of those matters.”
Declan McCullagh, writing for CNET, points out that this includes “all critical infrastructure sectors including energy, healthcare, and finance starting June 12.”
The documents reveal that the National Security Agency (NSA) and Defense Department were directly involved in pushing for this secret legal authorization.
NSA director Keith Alexander participated in some of the discussions personally, according to the documents.
Attorneys from the Justice Department signed off on the immunity despite the Department of Justice’s and industry participants’ initial reservations, according to CNET.
The legal immunity was given to participating internet service providers in the form of “2511 letters,” as the participants in the confidential discussions refer to them.
A 2511 letter is named after the Wiretap Act, 18 USC 2511, which the participants will not be held to by the Department of Justice.
According to CNET, “the 2511 letters provided legal immunity to the providers by agreeing not to prosecute for criminal violations of the Wiretap Act. It’s not clear how many 2511 letters were issued by the Justice Department.”
DIB Cyber Pilot was first publicly disclosed in 2011 by then Deputy Secretary of Defense William Lynn but in 2012, the pilot program expanded into an ongoing program dubbed Joint Cybersecurity Services Pilot. As of January it was renamed yet again, this time to Enhanced Cybersecurity Services program.
The same model used under the DIB pilot will be used under the new program, which means that participating companies “would be required to change their banners to reference government monitoring.”
The DHS privacy office stated that users on participating company networks will see “an electronic login banner [stating] information and data on the network may be monitored or disclosed to third parties, and/or that the network users’ communications on the network are not private.”
It is not clear how the banner will be worded exactly, but a 2011 Department of Defense Office of General Counsel PowerPoint presentation obtained by EPIC reveals eight of the elements that should be part of the banner:
1. It expressly covers monitoring of data and communications in transit rather than just accessing data at rest.
2. It provides that information transiting or stored on the system may be disclosed for any purpose, including to the Government.
3. It states that monitoring will be for any purpose.
4. It states that monitoring may be done by the Company/Agency or any person or entity authorized by Company/Agency.
5. It explains to users that they have “no [reasonable] expectation of privacy” regarding communications or data transiting or stored on the system.
6. It clarifies that this consent covers personal use of the system (such as personal emails or websites, or use on breaks or after hours) as well as official or work-related use.
7. It is definitive about the fact of monitoring, rather than conditional or speculative.
8. It expressly obtains consent from the user and does not merely provide notification.
“EPIC staff attorney Amie Stepanovich says the banner the government proposed is so broad and vague that it would allow ISPs not only to monitor the content of all communication, including private correspondence, but also potentially hand over the monitoring activity itself to the government,” Threat Level reports.
Similarly troubling is that it would only be seen by employees of participating companies, meaning that outsiders who communicate with those employees would have no clue that their communication was under surveillance.
“One of the big issues is the very broad notice and consent that they’re requiring, which far outpaces the description of the program the we’ve been given so far of not only the extent of the DIB pilot program but also the extent of the program that expands this to all critical infrastructure,” Stepanovich said, according to Threat Level.
“The concern is that information and communications between employees will be sent to the government, and they’re preparing employees to consent to this,” she added.
Both the NSA and Justice Department declined to comment to CNET but Sy Lee, a DHS spokesman sent a statement to CNET saying:
DHS is committed to supporting the public’s privacy, civil rights, and civil liberties. Accordingly, the department has implemented strong privacy and civil rights and civil liberties standards into all its cybersecurity programs and initiatives from the outset, including the Enhanced Cybersecurity Services program. In order to protect privacy while safeguarding and securing cyberspace, DHS institutes layered privacy responsibilities throughout the department, embeds fair practice principles into cybersecurity programs and privacy compliance efforts, and fosters collaboration with cybersecurity partners.
However, even individuals in the Justice Department “expressed misgivings that the program would ‘run afoul of privacy laws forbidding government surveillance of private Internet traffic,’” according to EPIC.
Furthermore, the Department of Homeland Security has no problem lying to Congress about their privacy breaches. Why anyone should believe that they would be honest now isn’t quite clear.
While the NSA claims they “will not directly filter the traffic or receive the malicious code captured by Internet providers,” EPIC points out that it is unclear how they can detect malicious code and prevent its execution without actually “captur[ing]” it in violation of federal law.
Former Homeland Security official Paul Rosenzweig likened the NSA and Defense Department asking the Justice Department for 2511 letters to “the CIA asking the Justice Department for the so-called torture memos a decade ago,” according to CNET.
“If you think of it poorly, it’s a CYA function,” Rosenzweig said. “If you think well of it, it’s an effort to secure advance authorization for an action that may not be clearly legal.”
This perspective was reinforced by a Congressional Research Service report published last month.
The report states it is likely the case that the executive branch does not actually have the legal authority to authorize additional widespread monitoring of communications unless Congress rewrites the law to give that authority.
“Such an executive action would contravene current federal laws protecting electronic communications,” the non-partisan report states.
However, CISPA – which the House passed last week – would actually give formal authorization to the program without resorting to workarounds like 2511 letters.
Since CISPA simply overrides any and all privacy laws at the state and federal level, any program like this would be given the legal green light.
Even more troubling is that the internal documents show that in late 2011, NSA, DoD and DHS officials actively met with aides on the House Intelligence committee who actually drafted the legislation.
“The purpose of the meeting, one e-mail shows, was to brief committee aides on ‘cyber defense efforts,’” as CNET put it.
Ryan Gillis, a director in the DHS Office of Legislative Affairs also sent an e-mail to Sen. Dianne Feinstein, a California Democrat and chairman of the Senate Intelligence Committee, discussing the pilot program during the same period.
It is hardly surprising that at least one of the same companies getting immunity under the 2511 letters has expressed support for CISPA, since both give network providers immunity from prosecution.
AT&T and CenturyLink are the only two providers publicly announcing their participation in the program thus far.
However, an unnamed government official cited by CNET said that other unnamed companies have signed a memorandum of agreement with DHS to join the program and are undergoing security certification.
“These agencies are clearly seeking authority to receive a large amount of information, including personal information, from private Internet networks,” Stepanovich said to CNET. “If this program was broadly deployed, it would raise serious questions about government cybersecurity practices.”
Rosenzweig points out that the expansion into the many sectors outlined in the executive order above could potentially even include the monitoring of meat packing plants.
Indeed, the language is broad enough to include just about anything at this point.
Reality Check - Internet Privacy Bill CISPA Means ‘No More Privacy’?
Google Involved in ‘Regime Change’: WikiLeaks

April 08, 2013 “Information Clearing House” -“Al-Akhbar” - Top Google execs, including the company’s CEO and one of Barack Obama’s major presidential campaign donors Eric Schmidt, informed the intelligence agency Stratfor about Google’s activities and internal communication regarding “regime change” in the Middle East, according to Stratfor emails released by WikiLeaks and obtained by Al-Akhbar. The other source cited was Google’s director for security and safety Marty Lev.
The briefings mainly focused on the movements of Jared Cohen, currently the director of Google Ideas, a “think/do-tank” billed as a vehicle for spreading American-style liberal democracy. Cohen was also a former member of US Secretary of State’s Policy Planning Staff and former advisor to Condoleezza Rice and Hillary Clinton.
Email exchanges, starting February 2011, suggest that Google execs were suspicious that Cohen was coordinating his moves with the White House and cut Cohen’s mission short at times for fear he was taking too many risks. Stratfor’s vice-president of counter-terrorism Fred Burton, who seemed opposed to Google’s alleged covert role in “foaming” uprisings, describes Cohen as a “loose Cannon” whose killing or kidnapping “might be the best thing to happen” to expose Google.
The Cohen Conspiracy
Stratfor’s spotlight on Cohen began on 9 February 2012 after Burton forwarded to the secure email list a Foreign Policy article discussing Cohen’s move from the State Department to Google Ideas. With this article, Burton noted that Cohen had dinner in Cairo with Wael Ghonim on January 27, 2011 just hours before the Egyptian Google Executive was famously picked up by Egypt’s State Security. (doc-id 1122191)
On the same day, Stratfor’s staff make reference to a Huffington Post article which highlighted Cohen’s role in “delaying the scheduled maintenance on Twitter so the Iranian revolution could keep going” and a Foreign Policy article that noted that Cohen “was a Rhodes scholar, spent time in Iran, [and] hung out in Iraq during the war…”. These casual discovers further perked Stratfor’s curiosity about Cohen. (doc-id 1629270)
The following day, Burton forwarded a message to the secure email list from “a very good Google source” who claimed that Cohen “[was] off to Gaza next week”. Burton added, “Cohen, a Jew, is bound to get himself whacked….Google is not clear if Cohen is operating [with a] State Dept [or] WH [White House] license, or [is] a hippie activist.”
Korena Zucha, another senior analyst on the list, queried, “Why hasn’t Google cut ties to Cohen yet? Or is Cohen’s activity being endorsed by those higher up in the [company] than your contact?”
In turn, Burton replied, “Cohen’s rabbi is Eric Schmidt and Obama lackey. My source is trying to find out if the billionaire owners are backing Cohen’s efforts for regime change.” (doc-id 1111729)
Later on, Burton forwarded information from the “Google source” of Cohen’s links in establishing Movements.org. The source added, “A site created to help online organization of groups and individuals to move democracy in stubborn nations. Funded through public-private partnerships.” Burton pointed out that the US State Department is the organization’s public sponsor.” (doc-id 1118344)
Indeed, the State Department, partnering with a number of corporations, was the main sponsor for the 2008 inaugural Alliance of Youth Movements summit in New York City that subsequently established Movements.org. Hillary Clinton endorsed the organization and presented a video message during the second summit held in Mexico City a year later.
On 11 February, Burton wrote to the secure email list that Cohen was still planning to head to Gaza. He added, “The dude is a loose can[n]on. GOOGLE is trying to stop his entry into Gaza now because the dude is like scorched earth. It’s unclear to GOOGLE if he’s driving without a license, but GOOGLE believes he’s on a specific mission of “regime change” on the part of leftist fools inside the WH who are using him for their agendas.” (doc-id 1113596)
Throughout this day, the idea proposed by Burton, and seemingly felt by his Google contacts as well, of Cohen and the White House’s involvement in the uprisings was actively discussed among the analysts, especially in regards to who would be targeted next. (doc-id 1113965)
By Monday, 14 February 2011, Burton shared intelligence with George Friedman, Stratfor’s founder, and Scott Stewart, vice-president of Stratfor’s tactical department, from his source in Google that Cohen was ordered not to go to Gaza. Burton’s Google source further stated, “Also, thinking I [the unnamed source] may be on the right track about him despite his denials [in reference to Cohen working for the White House/State Department].”
When asked to clarify his sources on Cohen, Burton claimed that they were Marty Lev, Google’s director for security and safety, and Eric Schmidt, the current CEO of Google. (doc-id 398679)
A week later, Burton forwarded an internal Google email obtained from a ‘senior Google executive’. This email was seemingly sent by Cohen to the senior Google executive to discuss Cohen’s planned trip in March.
In it, Cohen wrote, “I wanted to follow-up and get a sense of your latest thinking on the proposed March trip to UAE, Azerbaijan, and Turkey. The purpose of this trip is to exclusively engage the Iranian community to better understand the challenges faced by Iranians as part of one of our Google Ideas groups on repressive societies. Here is what we are thinking: Drive to Azerbaijan/Iranian border and engage the Iranian communities closer to the border (this is important because we need the Azeri Iranian perspective).”
After reading Cohen’s email, Stewart remarked, “Cohen might end up having an accident if he is not careful. This is not child’s play.”
Burton responded, “GOOGLE is getting WH [White House] and State Dept. support and air cover. In reality, they are doing things the CIA cannot do. But, I agree with you. He’s going to get himself kidnapped or killed. Might be the best thing to happen to expose GOOGLE’s covert role in foaming up-risings, to be blunt. The US Gov’t can then disavow knowledge and GOOGLE is left holding the shit bag.” (doc-id 1121800)
On 10 March 2011, Burton forwarded another message from his ‘senior Google executive’ source detailing how Cohen was requested not to travel on his proposed trip. The source explained that Google had concerns over Cohen’s “baggage” as a “US State Dept. policy maker, his research and publications on Muslim extremists and youth movements and his presence in Egypt just as the uprising started.”The source also stated that Cohen was recommended to “take a lower profile on this specific trip and let time pass before being visible and associated with people known by their states to be active in challenging repressive societies.” (doc-id 1164190)
A subsequent message from Burton’s source on 22 March 2011 affirmed that Cohen “heeded the advice not to go to Turkey or UAE for those meetings.” (doc-id 1133861)
The final email dealing with Cohen was on 30 March 2011.
Here, Burton forwarded to the alpha (secure) email list a response by his source to Burton’s question of whether Cohen was playing any role in Libya at the time. The source stated, “Not that I’m aware of. He heeded the advice to avoid Turkey and UAE and didn’t go on that trip.” (doc-id 1160182)
Google Ideas: Politicizing Technology
Certainly, there is more than meets the eye to Cohen and his actions; even his superiors in Google seem to think so.
The belief, chiefly by Burton, that Cohen had seemingly played a role in fermenting the uprisings that toppled Zine el Abidine Ben Ali and Hosni Mubarak underplays, and at times entirely disregards, the ability and agency by local movements in Tunisia and Egypt.
Nevertheless, Google Ideas, which Cohen directs, is a new animal. According to a report by the Financial Times published last July, Google Ideas seems to bond idealistic activist sensibilities with Google’s pursuit for continued global expansion - blurring the lines between business and political action. Schmidt and Cohen dub Google Ideas as a “think/do-tank” that aims to tackle political and diplomatic matters through the use of technology.
The first public event for the think/do-tank, in partnership with the Council on Foreign Relations and the Tribeca Film Festival, was held last June in Dublin. It gathered around 80 ‘former’ extremists, including former Muslim radicals, neo-Nazis, US gang members, and others, in a “Summit Against Violent Extremism”. The announcement by Google declared that the summit’s aim is “to initiate a global conversation on how best to prevent young people from becoming radicalised and how to de-radicalise others” and that “the ideas generated at the Dublin summit will be included in a study to be published later in the year.”
One spin off was the creation of the Against Violent Extremism group, apparently a network for those who attended the Dublin Summit. Beyond merely networking, the group also advertises certain projects that are in need of funding. Notably, much of the projects pertain to the Middle East, including an “Al-Awlaki Counter-Campaign” - Anwar al-Awlaki, an American citizen of Yemeni origin, was assassinated in September of last year by the US for his alleged al-Qaeda connections.
But the Against Violent Extremism site does not seem to be presently active. The last update for projects in need of funding was made in September and the last announcement regarding the workings of the site was made in October.
More recently, Foreign Policy reported in January that the Brookings Institute, one of the oldest and most influential think-tanks in Washington, DC, named Google Ideas as “the best new think tank established in the last 18 months.” Such accolades arguably suggests that Google Ideas is expected to be a major player in the near future.
Bitcoin wallet service Coinbase faces phishing attacks after data leak
(Arstechnica) -Bitcoin wallet service Coinbase has publicly, and presumably accidentally, exposed information about its users’ names, e-mail addresses, and details of their transactions on the Coinbase website. The exposed e-mail addresses have become the target of phishing attacks.
Coinbase, a Y Combinator-backed startup, is a popular service for holding users’ bitcoins. At the time of this writing, the leaked information was still showing up in Google searches of the Coinbase site:
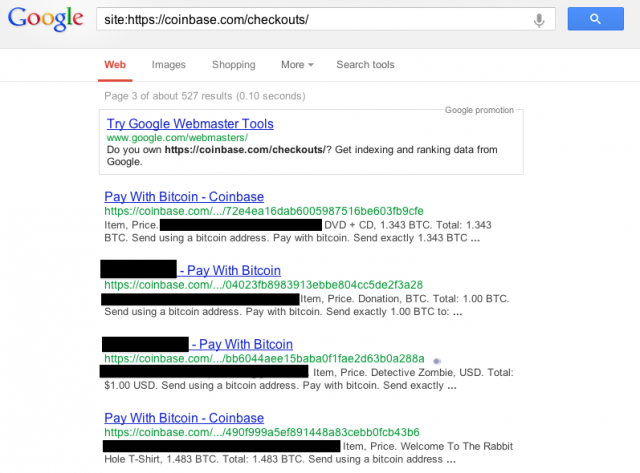
The URLs of the pages label them “checkouts,” and they appear to be transaction receipts. One was a 0.05 BTC ($6.85) transaction labeled as a donation. Another was a $980 transaction for “8 managed VPS hosts” from a company called cachedd. A third was a 229.99 BTC ($31,508) trasnsaction for “AVALANCHE SPA POWDER.”
In a Thursday blog post, Coinbase warned users to “beware of a phishing attack.” Someone has been sending e-mails to Coinbase users claiming that they need to log in to confirm recent transactions but directing them to a website not controlled by Coinbase. Late Friday morning, the leaked information was still publicly available on the Coinbase website.
There’s no evidence of a security problem with the Coinbase site. Provided users don’t fall for the phishing scheme, their funds should be safe. But publicly exposing users’ contact information and transaction details is a pretty big screwup.
We’ve emailed Coinbase seeking comment and will update if they respond.
Watch Out for Google Glasses
NEW YORK (TheStreet) — By the end of this year, our society will undergo a most peculiar form of societal change — and it will involve a lot of strife and conflict. The cause? Google(GOOG_) Glasses.
Yes, every smartphone can record you and take pictures. But you know when this is happening. It isn’t a constant feeling that everyone around you is filming you from every angle. You see them when they do it.
Google Glasses are different. More than just photos and filming, what happens to this data?
Let’s say that I’m standing behind the counter at a businessestablishment — bank, fast-food restaurant, airline check-in counter, whatever. My Google Glasses might display the social security number, the general rap sheet, social media appearances, and so on, of the person in front of me.
Perhaps that’s a good thing. Some people will think it’s creepy, though. Can you imagine the bar scene when people start wearing Google Glasses? Within a second or two, you will have all available information about the person in front of you. Some of that information may not be so flattering.
Public places will have to come up with new policies. Hotels, airports, restaurants, gyms and schools will want some say in whether you are allowed to wear these Google Glasses on their premises. You can just hear the panic buttons after the first pictures from people cheating in school or filming in the locker room are released on YouTube. Conflicts about are certain to get very ugly.
Other dimensions immediately appear. What if future versions of Google Glasses are very difficult to detect in terms of looking different from regular glasses?
What happens when you walk into an establishment today wielding a video camera in the faces of the staff? In a restaurant, a bank lobby, or a gym? You will be asked to turn that thing off, and if you don’t obey quickly, you will be escorted from the premises.
Google Glasses will make all social/public interaction highly awkward. You’re on YouTube everywhere you go. A few short months after their introduction, Google Glasses could already be so widespread that you will be on camera once you stick your nose out your front door.
Privacy lawyers, saddle up!
The Google Glasses data captured in the form of pictures and videos will not only be used by the person wearing the glasses. The person capturing the images may want to “auto-tag” these media with the identities of the people in the picture/video.
Some people prefer to stay off the grid. They pay cash, they drive a car without GPS, they don’t have a cell phone, and they’re not members of online social networks. They have been able to stay out of most publicly available databases.
Once a meaningful percentage of people start walking down the street wearing Google Glasses, not so much. There will be no place to hide — unless the government legislates Google Glasses, or private establishments decide to ban them.
What about Google itself?
Google Glasses will be the critical ingredient in the personal information arms race of the (soon to arrive) future. If other people wear them, why shouldn’t I? I predict that everyone with means will rush to obtain them, especially as the price falls from $1,500 to $1,000 to $500 and eventually below, over the first two years.
If Google succeeds in bringing these kinds of glasses to market before key competitors, most notably Apple(AAPL_), but also Microsoft(MSFT_), the advantage could prove to be decisive. Google already has a 70% smartphone market share with Android, so it’s pretty much already there, but don’t forget the Microsoft’s market share in the PC business was close to 95% until only a few short years ago.
Seeing as Google is likely to engineer some sort of tie-in between the Glasses and Android smartphones, the Glasses should be a tremendous boon for Android. Anyone looking at their iPhone would have to seriously consider switching.
Google Glasses may cause societal chaos, but they will be great for Google’s finances.
Surge in user info requests from govts: Google
Google said it had received 21,389 applications from government officers and the courts over the last six months of 2012. That is 17 percent up on the same period the previous year, and 71 percent more than 2009’s corresponding months.
Authorities in the US delivered nearly 8,438 of the requests, representing nearly 40 percent of the worldwide total. The US volume was one-third higher than in the same period the previous year.
Subpoenas accounted for 68 per cent of US requests, followed by search warrants at 22 per cent. A mix of court orders and other legal demands made up the remaining US requests for user information from Google.
India generated the second highest number of user requests during the final half of last year at 2,431, a 10 per cent increase from the previous year.
The figures include requests related to its YouTube video service.
Google said it handed over at least some data in 66 percent of the most recent cases.
The number of requests has risen over every half-year cycle since Google started publishing details three years ago.
The US made more requests than any other country with 8,438 submissions. Google complied fully or partially with 88 percent of these.
By contrast all of Turkey’s 149 requests and Hungary’s 95 applications were rejected outright. The UK made 1,458 requests - a very slight rise on the same period in 2011. 70 percent of them resulted in some information being provided.
One UK-based privacy advocacy group praised Google for releasing the data, but said it also served as a warning to individuals to be careful about the information they passed on to any online business.
Carly Nyst, Privacy International’s head of international advocacy, said the information they hand over to companies like Google merits the highest degree of privacy and security, and should only be accessed by third parties under exceptional circumstances.
Nyst added that governments should stop treating the user data held by corporations as a treasure trove of information they can mine whenever they please, with little or no judicial authorization.
Google said it would publish details of removal requests at a later time.
Google aims to replace passwords with ID ring

They have added to growing claims that passwords are both inherently insecure and increasingly impractical.
To more make them more difficult for criminals to guess, web services have forced people to use longer passwords with different types of characters, but that also makes them more difficult to remember. To add to the headache, experts also advise against using the same password for different services, to reduce the impact if one is hacked.
“Along with many in the industry, we feel passwords and simple bearer tokens such as cookies are no longer sufficient to keep users safe,” said Google vice president of security Eric Grosse and engineer Mayank Upadhyay, in an article to be published in an engineering journal.
Cookies are small text files issued by websites to web browser software to keep visitors logged in once they have entered their password.
“We’d like your smartphone or smartcard-embedded finger ring to authorize a new computer via a tap on the computer, even in situations in which your phone might be without cellular connectivity,” the Googlers wrote.
Grosse and Upadhyay said they are currently experimenting with YubiKey, a tiny USB stick that implements highly secure “one time pad” cryptography to log in to Google services, as a replacement for passwords. In the future, they want similar authentication technology to work wirelessly and across all of a person’s online accounts.
“We’ll have to have some form of screen unlock, maybe passwords but maybe something else,” Grosse said, Wired reports. “But the primary authenticator will be a token like this or some equivalent piece of hardware.”
Security experts have pointed to the problems with passwords for years, and suggested alternatives, but none have been widely adopted because they would require web services to adopt standards.
Grosse and Upadhyay’s paper is attracting attention because coming from the world’s biggest web company, it may stand a better chance of success.
“Others have tried similar approaches but achieved little success in the consumer world,” Grosse and Upadhyay wrote.
“Although we recognize that our initiative will likewise remain speculative until we’ve proven large scale acceptance, we’re eager to test it with other websites.”
Given the rivalries online and the low cost and ubiquity of passwords, progress remains a tall order, however. Bill Gates predicted the death of passwords at a security conference in 2004.
Quentin Tarantino’s blow-up at Channel 4 News: good for him
 Quentin Tarantino tells C4 news presenter Krishnan Guru-Murthy exactly what he thinks of his questions. Link to this video
Quentin Tarantino tells C4 news presenter Krishnan Guru-Murthy exactly what he thinks of his questions. Link to this video
(Guardian.co.uk) I am no fan of the slavery revenge western Django Unchained but you will meet few people more enthusiastic than I was about the abrasive, straight-shooting television interview given this week by its writer-director Quentin Tarantino to Channel 4 News. The presenter Krishnan Guru-Murthy began by trying to explore Tarantino’s interest in making violent films, only to be met with a polite brush-off: Judd Apatow doesn’t get asked why he makes comedies, the director reasoned. So far, so logical. But then he tried to prod Tarantino into reflecting on whether there was any link between violence in movies and in real life. “It’s none of your damn business what I think about that,” came the reply, “I’m saying ‘no’… If anyone cares what I have to say about it, they can Google me.”
Guru-Murthy remained immobile in his seat, as Tarantino ranted and raved, giving the impression that his eyes were going to pop from their sockets. He also provided the first instance of the phrase “I’m shutting your butt down!” I’ve ever seen on British TV.
The problem here was not the issue of violence itself, but the wearisome ploughing of the same furrow. You’ve got Quentin Tarantino sitting in front of you, one of the most stimulating interviewees in the world, and you ask him questions that he was unpicking 21 years ago when he promoted his debut Reservoir Dogs? Tarantino’s indignant response was proportionate and refreshing.
His prickliness should not detract from the points he scored against this pious style of questioning to which many news programmes resort whenever they are called upon to report on anything that intersects with popular culture. Like Graham Linehan, who objected on-air to the Today programme’s bear-baiting discussion tactics over his stage adaptation of The Ladykillers, Tarantino refused to adhere to this rigged news agenda.
The promotional tour for the director’s extravagantly violent and provocative fantasy was never going to resemble the usual round of red-carpet gladhanding. And it’s true that the path to PR glory has already encountered a few interesting speed-bumps: there was the mischievous attempt by one of the film’s stars, Samuel L Jackson, to goad an affable white interviewer into uttering the n-word, which features prominently in the movie’s dialogue. And this week there was some discomfort expressed over the decision to market collectible Django Unchained action figures. Even though these 8-inch dolls are designed for memorabilia nuts rather than Toys R Us, there’s still something disconcerting about the collision of merchandising and what Tarantino himself calls “the Auschwitzian aspect of the slave trade.” But this is emblematic of the film itself, which deliberately examines an era of traumatic historical injustice through the grime-tinted glasses of the exploitation genre.
The Channel 4 News argument didn’t address the meagre merits and political shortcomings of Django Unchained. Nevertheless, the rare glimpse it allows us behind the PR curtain is invaluable. It makes me recall the time I put a question to the director Abel Ferrara, who proceeded to slip into a dense and restful slumber before I had finished speaking. Or the afternoon I was standing outside a hotel room awaiting a private audience with Martin Scorsese, only to overhear him complaining that he had done enough interviews for one day. “I’m all wiped out,” he protested loudly to his assistant. “I don’t know how I’m gonna do Germany. I’ll do it, but I don’t know how.” Poor me. And, for that matter, poor Germany.
The demands of the relentless publicity treadmill can lead to compromises on all fronts: the subject can be crotchety, the interviewer nervous and hurried, and nobody gets what they want. The inanity of being quizzed by the same jaded journalists competing for identical soundbites was the catalyst for Tarantino’s blow-up. To be fair to journalists, the situation doesn’t always work in our favour: spending between 10 and 30 minutes with your subject in a hotel room is unlikely to produce relaxed and forthcoming testimonies. But then it’s the journalist’s job to use that small window of time to pose the most disarming and unusual enquiries they can manage.
It was perhaps ungracious of Tarantino to bellow: “I’m here to sell my movie! This is a commercial for the movie, make no mistake.” But I am inclined to blame tiredness, maybe jet-lag, since he is usually a witty interviewee. During the hour I spent with him in 2009 discussing his last picture, Inglourious Basterds, he was brilliantly, intelligently combative in a way which is rare in the mollycoddled trade-offs between movies and media.
Had he been less weary, he might have taken umbrage earlier in the Channel 4 interview, when Guru-Murthy asked “Why do you love violent movies?” That inane remark hardly takes into account the extraordinary sophistication of violence in Tarantino’s work: from the camera steering away from an ear-severing scene in Reservoir Dogs to the various murders-in-long-shot in Jackie Brown, or the Busby Berkeley approach to shooting mass carnage in Kill Bill, Vol 1. If only the line of questioning on Channel 4 News had been as nuanced and considered as one of Tarantino’s movies.
Google starts watching what you do off the Internet too
(RT) - The most powerful company on the Internet just got a whole lot creepier: a new service from Google merges offline consumer info with online intelligence, allowing advertisers to target users based on what they do at the keyboard and at the mall.
Without much fanfare, Google announced news this week of a new advertising project, Conversions API, that will let businesses build all-encompassing user profiles based off of not just what users search for on the Web, but what they purchase outside of the home.
In a blog post this week on Google’s DoubleClick Search site, the Silicon Valley giant says that targeting consumers based off online information only allows advertisers to learn so much. “Conversions,” tech-speak for the digital metric made by every action a user makes online, are incomplete until coupled with real life data, Google says.
“We understand that online advertising also fuels offline conversions,” the blog post reads. Thus, Google says, “To capture these lost conversions and bring offline into your online world, we’re announcing the open beta of our Conversions API for uploading offline conversion automatically.”
The blog goes on to explain that in-store transactions, call-tracking and other online activities can be inputted into Google to be combined with other information “to optimize your campaigns based on even more of your business data.”
Google is all but certain to ensure that all user data collected off- and online will be cloaked through safeguards that will allow for complete and total anonymity for customers. When on-the-Web interactions start mirroring real life activity, though, even a certain degree of privacy doesn’t make Conversions API any less creepy. As Jim Edwards writes for Business Insider, “If you bought a T shirt at The Gap in the mall with your credit card, you could start seeing a lot more Gap ads online later, suggesting jeans that go with that shirt.”
Of course, there is always the possibility that all of this information can be unencrypted and, in some cases, obtained by third-parties that you might not want prying into your personal business. Edwards notes in his report that Google does not explicitly note that intelligence used in Conversions API will be anonymized, but the blowback from not doing as much would sure be enough to start a colossal uproar. Meanwhile, however, all of the information being collected by Google — estimated to be on millions of servers around the globe — is being handed over to more than just advertising companies. Last month Google reported that the US government requested personal information from roughly 8,000 individual users during just the first few months of 2012.
“This is the sixth time we’ve released this data, and one trend has become clear: Government surveillance is on the rise,” Google admitted with their report.


