Activist Post
 According to documents obtained by the Electronic Privacy Information Center (EPIC), the Department of Justice secretly authorized the interception of electronic communications on certain parts of AT&T and other Internet service providers’ networks.
According to documents obtained by the Electronic Privacy Information Center (EPIC), the Department of Justice secretly authorized the interception of electronic communications on certain parts of AT&T and other Internet service providers’ networks.
Previously, EPIC obtained documents on the National Security Agency’s Perfect Citizen program which involves monitoring private computer networks. This latest revelation deals with an entirely different program first called Defense Industrial Base Cyber Pilot, or DIB Cyber Pilot, though it is now operating as Enhanced Cybersecurity Services.
While this type of activity might be illegal under federal wiretapping legislation, the Obama administration gave the companies immunity when monitoring networks under a cybersecurity pilot program.
“The Justice Department is helping private companies evade federal wiretap laws,” said Marc Rotenberg, executive director of EPIC. “Alarm bells should be going off.”
The alarm bells should get louder when one realizes that while this collaboration between the Department of Defense (DoD), the Department of Homeland Security (DHS) and the private sector began focusing only on defense contractors, the program was massively expanded.
Thanks to an executive order dated February 12, 2013 entitled, “Improving Critical Infrastructure Cybersecurity,” the program was widened significantly.
The order expanded it to cover other “critical infrastructure industries” which includes “systems and assets, whether physical or virtual, so vital to the United States that the incapacity or destruction of such systems and assets would have a debilitating impact on security, national economic security, national public health or safety, or any combination of those matters.”
Declan McCullagh, writing for CNET, points out that this includes “all critical infrastructure sectors including energy, healthcare, and finance starting June 12.”
The documents reveal that the National Security Agency (NSA) and Defense Department were directly involved in pushing for this secret legal authorization.
NSA director Keith Alexander participated in some of the discussions personally, according to the documents.
Attorneys from the Justice Department signed off on the immunity despite the Department of Justice’s and industry participants’ initial reservations, according to CNET.
The legal immunity was given to participating internet service providers in the form of “2511 letters,” as the participants in the confidential discussions refer to them.
A 2511 letter is named after the Wiretap Act, 18 USC 2511, which the participants will not be held to by the Department of Justice.
According to CNET, “the 2511 letters provided legal immunity to the providers by agreeing not to prosecute for criminal violations of the Wiretap Act. It’s not clear how many 2511 letters were issued by the Justice Department.”
DIB Cyber Pilot was first publicly disclosed in 2011 by then Deputy Secretary of Defense William Lynn but in 2012, the pilot program expanded into an ongoing program dubbed Joint Cybersecurity Services Pilot. As of January it was renamed yet again, this time to Enhanced Cybersecurity Services program.
The same model used under the DIB pilot will be used under the new program, which means that participating companies “would be required to change their banners to reference government monitoring.”
The DHS privacy office stated that users on participating company networks will see “an electronic login banner [stating] information and data on the network may be monitored or disclosed to third parties, and/or that the network users’ communications on the network are not private.”
It is not clear how the banner will be worded exactly, but a 2011 Department of Defense Office of General Counsel PowerPoint presentation obtained by EPIC reveals eight of the elements that should be part of the banner:
1. It expressly covers monitoring of data and communications in transit rather than just accessing data at rest.
2. It provides that information transiting or stored on the system may be disclosed for any purpose, including to the Government.
3. It states that monitoring will be for any purpose.
4. It states that monitoring may be done by the Company/Agency or any person or entity authorized by Company/Agency.
5. It explains to users that they have “no [reasonable] expectation of privacy” regarding communications or data transiting or stored on the system.
6. It clarifies that this consent covers personal use of the system (such as personal emails or websites, or use on breaks or after hours) as well as official or work-related use.
7. It is definitive about the fact of monitoring, rather than conditional or speculative.
8. It expressly obtains consent from the user and does not merely provide notification.
“EPIC staff attorney Amie Stepanovich says the banner the government proposed is so broad and vague that it would allow ISPs not only to monitor the content of all communication, including private correspondence, but also potentially hand over the monitoring activity itself to the government,” Threat Level reports.
Similarly troubling is that it would only be seen by employees of participating companies, meaning that outsiders who communicate with those employees would have no clue that their communication was under surveillance.
“One of the big issues is the very broad notice and consent that they’re requiring, which far outpaces the description of the program the we’ve been given so far of not only the extent of the DIB pilot program but also the extent of the program that expands this to all critical infrastructure,” Stepanovich said, according to Threat Level.
“The concern is that information and communications between employees will be sent to the government, and they’re preparing employees to consent to this,” she added.
Both the NSA and Justice Department declined to comment to CNET but Sy Lee, a DHS spokesman sent a statement to CNET saying:
DHS is committed to supporting the public’s privacy, civil rights, and civil liberties. Accordingly, the department has implemented strong privacy and civil rights and civil liberties standards into all its cybersecurity programs and initiatives from the outset, including the Enhanced Cybersecurity Services program. In order to protect privacy while safeguarding and securing cyberspace, DHS institutes layered privacy responsibilities throughout the department, embeds fair practice principles into cybersecurity programs and privacy compliance efforts, and fosters collaboration with cybersecurity partners.
However, even individuals in the Justice Department “expressed misgivings that the program would ‘run afoul of privacy laws forbidding government surveillance of private Internet traffic,’” according to EPIC.
Furthermore, the Department of Homeland Security has no problem lying to Congress about their privacy breaches. Why anyone should believe that they would be honest now isn’t quite clear.
While the NSA claims they “will not directly filter the traffic or receive the malicious code captured by Internet providers,” EPIC points out that it is unclear how they can detect malicious code and prevent its execution without actually “captur[ing]” it in violation of federal law.
Former Homeland Security official Paul Rosenzweig likened the NSA and Defense Department asking the Justice Department for 2511 letters to “the CIA asking the Justice Department for the so-called torture memos a decade ago,” according to CNET.
“If you think of it poorly, it’s a CYA function,” Rosenzweig said. “If you think well of it, it’s an effort to secure advance authorization for an action that may not be clearly legal.”
This perspective was reinforced by a Congressional Research Service report published last month.
The report states it is likely the case that the executive branch does not actually have the legal authority to authorize additional widespread monitoring of communications unless Congress rewrites the law to give that authority.
“Such an executive action would contravene current federal laws protecting electronic communications,” the non-partisan report states.
However, CISPA – which the House passed last week – would actually give formal authorization to the program without resorting to workarounds like 2511 letters.
Since CISPA simply overrides any and all privacy laws at the state and federal level, any program like this would be given the legal green light.
Even more troubling is that the internal documents show that in late 2011, NSA, DoD and DHS officials actively met with aides on the House Intelligence committee who actually drafted the legislation.
“The purpose of the meeting, one e-mail shows, was to brief committee aides on ‘cyber defense efforts,’” as CNET put it.
Ryan Gillis, a director in the DHS Office of Legislative Affairs also sent an e-mail to Sen. Dianne Feinstein, a California Democrat and chairman of the Senate Intelligence Committee, discussing the pilot program during the same period.
It is hardly surprising that at least one of the same companies getting immunity under the 2511 letters has expressed support for CISPA, since both give network providers immunity from prosecution.
AT&T and CenturyLink are the only two providers publicly announcing their participation in the program thus far.
However, an unnamed government official cited by CNET said that other unnamed companies have signed a memorandum of agreement with DHS to join the program and are undergoing security certification.
“These agencies are clearly seeking authority to receive a large amount of information, including personal information, from private Internet networks,” Stepanovich said to CNET. “If this program was broadly deployed, it would raise serious questions about government cybersecurity practices.”
Rosenzweig points out that the expansion into the many sectors outlined in the executive order above could potentially even include the monitoring of meat packing plants.
Indeed, the language is broad enough to include just about anything at this point.






 Vulnerabilities in the management interfaces of some wireless router and network-attached storage products from Netgear expose the devices to remote attacks that could result in their complete compromise, researchers warn.
Vulnerabilities in the management interfaces of some wireless router and network-attached storage products from Netgear expose the devices to remote attacks that could result in their complete compromise, researchers warn. 
 This is an (admittedly huge) list of words that supposedly cause the NSA to flag you as a potential terrorist if you over-use them in an email.
This is an (admittedly huge) list of words that supposedly cause the NSA to flag you as a potential terrorist if you over-use them in an email. 




 According to documents obtained by the Electronic Privacy Information Center (EPIC), the Department of Justice secretly authorized the interception of electronic communications on certain parts of AT&T and other Internet service providers’ networks.
According to documents obtained by the Electronic Privacy Information Center (EPIC), the Department of Justice secretly authorized the interception of electronic communications on certain parts of AT&T and other Internet service providers’ networks.
 It’s not really feasible for each of us to track each piece of information to its source (nor would it be efficient), so, instead, we use clues — who wrote this, where is this published, does this square with other information we know. But the trouble is that these clues aren’t perfect indicators, at least in part because even credible publications and professional journalists sometimes regurgitate information without giving it a careful vetting, a process often referred to as churnalism (just as gross as it sounds).
It’s not really feasible for each of us to track each piece of information to its source (nor would it be efficient), so, instead, we use clues — who wrote this, where is this published, does this square with other information we know. But the trouble is that these clues aren’t perfect indicators, at least in part because even credible publications and professional journalists sometimes regurgitate information without giving it a careful vetting, a process often referred to as churnalism (just as gross as it sounds). Boston entered a lockdown state Friday and rumours about unexploded bombs circulated on social media. (Brian Snyder/Reuters)
Boston entered a lockdown state Friday and rumours about unexploded bombs circulated on social media. (Brian Snyder/Reuters)

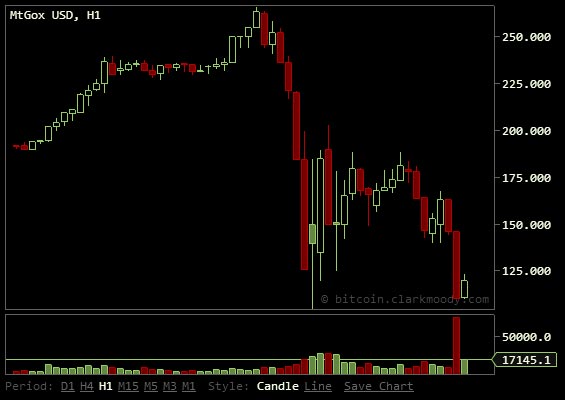
 Just a few months ago the total net worth of all Bitcoins, a popular encrypted digital currency, was worth about $140 million. The non-tangible exchange mechanism is used by people all over the world to purchase everything from traditional goods and services, to illicit trade that may include drugs and stolen credit card numbers. The coins became a go-to digital store of wealth around the world after the meltdown of the Cypriot financial system, and was pushed as a ‘safe’ way to preserve wealth out of view prying government eyes. All of the excitement surrounding Bitcoin has driven the price of a single unit to in excess of $250, giving the total Bitcoins in global circulation a
Just a few months ago the total net worth of all Bitcoins, a popular encrypted digital currency, was worth about $140 million. The non-tangible exchange mechanism is used by people all over the world to purchase everything from traditional goods and services, to illicit trade that may include drugs and stolen credit card numbers. The coins became a go-to digital store of wealth around the world after the meltdown of the Cypriot financial system, and was pushed as a ‘safe’ way to preserve wealth out of view prying government eyes. All of the excitement surrounding Bitcoin has driven the price of a single unit to in excess of $250, giving the total Bitcoins in global circulation a 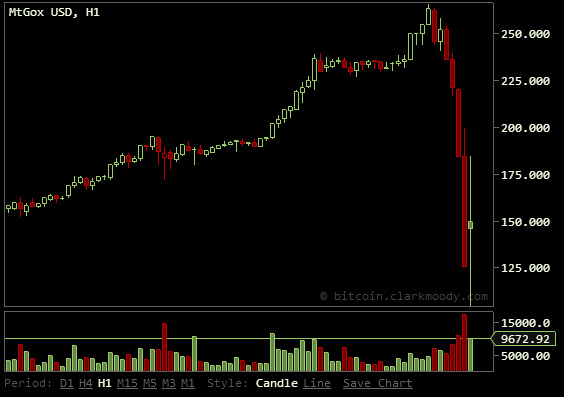 (Chart Courtesy
(Chart Courtesy 
 (www.sherriequestioningall.blogspot.com) Well is it any wonder they want to wipe out every single Bill of Rights we have? We have had only 2 left, the 2nd amendment (they are working on) and the 1st amendment (up to a point).
(www.sherriequestioningall.blogspot.com) Well is it any wonder they want to wipe out every single Bill of Rights we have? We have had only 2 left, the 2nd amendment (they are working on) and the 1st amendment (up to a point). (Washington Post) Federal investigators looking into disclosures of classified information about a cyberoperation that targeted Iran’s nuclear program have increased pressure on current and former senior government officials suspected of involvement, according to people familiar with the investigation.
(Washington Post) Federal investigators looking into disclosures of classified information about a cyberoperation that targeted Iran’s nuclear program have increased pressure on current and former senior government officials suspected of involvement, according to people familiar with the investigation.

 The Immigration Sharing Treaty, an integral part of the
The Immigration Sharing Treaty, an integral part of the